The DNS is a massive tree of names containing all the names on the Internet. But it has a single starting point: the DNS root zone. The DNS root zone is the parent of all the DNS TLDs. The DNS root zone gives the DNS a single point to begin. You can find any DNS name in the world starting from the DNS root zone!

The DNS as a tree of names
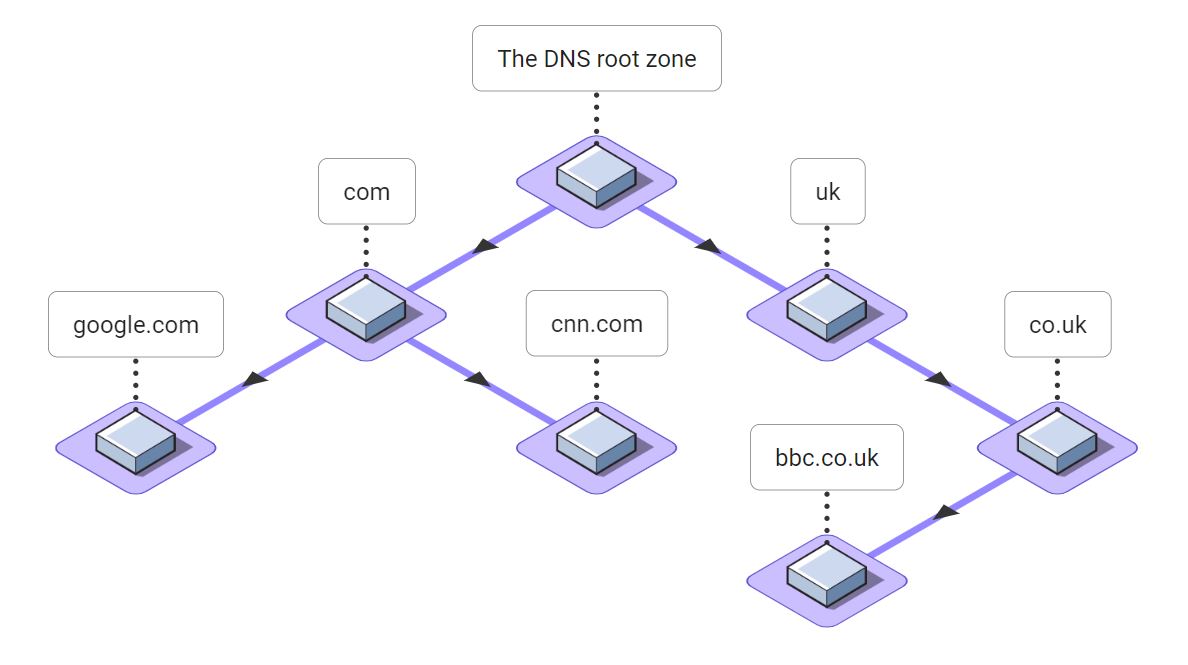
It’s helpful to dissect a few DNS names to understand how the DNS forms a tree and where the “root” of the tree lies. Consider a few popular DNS names: google.com, cnn.com, and bbc.co.uk.
The right-most label in all DNS names is always a Top Level Domain (TLD) such as .com or .uk. Below the TLDs are the next labels in domain names like google.com. So below .com we find google.com, and below .uk we find co.uk. Each time we move downwards in the DNS tree, another label is added to the left side of the DNS name.
We can put these relationships together in a picture that looks like a tree with a single node at the top and the branches (or roots, if you prefer) extending downward. We can see that .com is the parent of google.com and co.uk is the parent of bbc.co.uk, and so on. All DNS names fall somewhere in this tree.
But what is the parent of .com and .uk and all other TLDs? The answer is the DNS root zone. The DNS root zone is the parent of all the DNS TLDs. It is the starting point for the entire DNS.
The DNS is a global hierarchical database
The DNS was envisioned as a single database for all the names on what would become the Internet. But because many different organizations would own the names in the DNS, it was designed to be hierarchical. The DNS root zone gives this massive database of names a single starting point. Hence the name root zone.
DNS resolvers use a process called recursion to resolve names by starting at the DNS root zone. Resolvers follow pointers called delegations from the DNS root zone down the DNS tree to eventually arrive at the answer, which is often the address of a web server such as www.google.com.
The beauty of the DNS is that if you know how to contact a single server for the DNS root zone, you can resolve any name in the entire DNS!
What are DNS zones?
You may be wondering what a zone is if you are new to DNS. Our article, What is a DNS zone? may be helpful.
A DNS zone is a portion of the DNS namespace owned and managed by a specific person, corporation, or other entity. Each label in a DNS name, the string of characters between periods, may represent a new DNS zone. Other labels may represent names within a zone. As an example, let’s consider all of the labels involved in the DNS name www.google.com:
- At the top is the root zone. The root zone is the parent of all of the TLDs. Technically the root zone’s name is the empty string.
- Next is the .com zone. This is one of the Internet TLDs. All names in the DNS lie below a TLD.
- Below .com we have google.com. This is the DNS zone owned by Google.
- Lastly, www.google.com is a DNS name within the google.com zone managed by Google.
Who oversees the root zone?
The DNS is the lifeblood of the Internet: without the DNS, virtually every online resource would be unavailable. And the DNS root zone is the most critical part of the DNS since resolving any DNS name begins at the root zone. So who owns and operates the DNS root zone?
Operation of the DNS root zone is overseen by ICANN (Internet Corporation for Assigned Names and Numbers). ICANN not only oversees the root zone. It also manages domain name registries and IP addresses to ensure the stability of the Internet, and to foster competition and customer choice.
The United States Department of Commerce directly oversaw ICANN for many years. In 2017, ICANN transitioned to a global multi-stakeholder model, but even today the US government has a significant amount of power over the root zone.
How many servers host the root zone?
Anyone can view the set of NS records for the root zone. There are many online DNS lookup tools, or you can use the popular DNS command line tool dig. This command tells dig to retrieve the NS records for the DNS root (denoted by “.”) and return the short form of the output:
dig +short ns . a.root-servers.net. b.root-servers.net. c.root-servers.net. d.root-servers.net. e.root-servers.net. f.root-servers.net. g.root-servers.net. h.root-servers.net. i.root-servers.net. j.root-servers.net. k.root-servers.net. l.root-servers.net. m.root-servers.net.
If you don’t have dig, you can view the same information using the nslookup command line tool: nslookup -q=ns .
From this list, there are 13 NS records for the DNS root. They have very regular names: a through m, followed by root-servers.net. Each of these NS records represents a DNS root server. But behind each NS name is a cluster of servers tied together using Anycast routing. Anycast allows many servers to act as one. When a DNS resolver sends a query to one of the root server addresses, the query is automatically routed to one of these many individual servers.
So while there are 13 DNS root server names, there are currently over 1600 individual root server instances worldwide, according to root-servers.org.
How does a recursive DNS server find root server IP addresses?
The DNS root servers have names like a.root-servers.net. But since DNS is used to map names to IP addresses, how do recursive DNS servers find the IP addresses of the root servers without ending up in a infinite circular loop?
The answer is that all recursive DNS servers come pre-provisioned with a root hints file. For historical reasons this file is often called named.root. This file contains the IP addresses of the DNS root servers. The current official version of this file is maintained by Internic.
It is possible that these IP addresses may change, although that does not happen often. DNS recursive resolvers try all of the root server IP addresses from the root hints file until one responds. So even if one or more of the IP addresses changes, they will still be able to find the DNS root zone.
Who operates each DNS root server?
The root zone itself is overseen by ICANN. The operation of the 13 individual root servers is contracted out to various organizations:
- a.root-servers.net: Verisign, Inc.
- b.root-servers.net: University of Southern California, Information Sciences Institute
- c.root-servers.net: Cogent Communications
- d.root-servers.net: University of Maryland
- e.root-servers.net: NASA (Ames Research Center)
- f.root-servers.net: Internet Systems Consortium, Inc.
- g.root-servers.net: US Department of Defense (NIC)
- h.root-servers.net: US Army (Research Lab)
- i.root-servers.net: Netnod
- j.root-servers.net: Verisign, Inc.
- k.root-servers.net: RIPE NCC
- l.root-servers.net: ICANN
- m.root-servers.net: WIDE Project
You can find this list, along with the Anycast IP addresses of each root server at the Internet Assigned Numbers Authority (IANA).
Many of the DNS root servers are operated by American organizations and some are operated by the United States military. This dependence on the United States is a common criticism of the DNS, and the operation of the Internet in general.
Why are there exactly 13 root servers?
As we have seen, there are 13 NS records for the DNS root zone, and hence officially, there are 13 root servers. With many more servers operating behind the scenes through the magic of Anycast routing. But why the “unlucky” number thirteen?
The answer has to do with size of a DNS message on the Internet. Originally, DNS messages had to be kept below 512 bytes in size for efficiency. It turns out that 13 NS records plus one A record for each fits almost exactly into 512 bytes!
Another interesting side note is that the DNS names of the root servers were selected to be so similar to one another so that DNS name compression can more efficiently pack the NS records into DNS messages.
How many TLDs are in the root zone?
When the DNS root zone was first created, there were only a handful of Top Level Domains (TLDs) such as com, org, and net. Over time the number of TLDs has exploded. Today, there are currently 1,480 TLDs!
There are different types of TLDs, including:
- Generic TLDs (gTLDs): This group includes the popular .com, .org, .net, and .info. But also many more. These TLDs are open to anyone to register in without restriction. Most TLDs, currently over 1200, fall into this group.
- Sponsored TLDs (sTLDs): These TLDs are supervised by private organizations. The organizing body has the final say over whether a new name can be registered in their sTLD. Some popular sTLDs include .edu, .gov, and .travel.
- Country Code TLDs (ccTLDs): These TLDs were each created for a specific country, such as .ca for Canada and .uk for the United Kingdom. But many ccTLDs are used to create catchy domain names without regard for domain’s actual country. For example, YouTube uses .be (Belgium) to create video links at youtu.be, and Microsoft often uses .ms (Montserrat). This practice is sometimes called “name hacking”.
- Infrastructure TLDs: There is only one infrastructure TLD: .arpa. This TLD contains reverse mappings for IP addresses using PTR records.
- Test TLDs: These are TLDs reserved for testing by RFC 2606. It includes .test, .example, .invalid, and .localhost.
IANA publishes the official list of TLDs, and the DNS root zone file is published for everyone to see by Internic.
Are there other DNS root zones?
Many attempts have been made to create alternative root zones, dating back to at least 1995. Alternative roots, or altroots, have been created either for profit or for ideological reasons. Often to protest the way the Internet root zone has been centrally governed. China and Russia have been working on alternative roots to restrict and control the flow of information to their citizens.
These altroot projects have had limited success, and many have become defunct. This is largely because it is difficult for non-technical users to easily access them. There have been a number projects involving browser extensions to try to make altroots easier to use, but they still enjoy limited success.
A thorough list of past and present alternative roots can be found at icannwiki.org.
Decentralizing the DNS
A common criticism of the DNS is that while it is globally distributed, it is based on a centralized model of trust. And additionally that the United States ultimately controls, or at least strongly influences, too much of the operation of the DNS.
The most recent attempt to create an alternative DNS root, and in fact an alternative to the current DNS entirely, is based on blockchain. Namecoin is a prominent example.
An alternative to DNS based on blockchain could solve many problems with the DNS:
- DDoS: The DNS is vulnerable to large-scale Distributed Denial of Service (DDoS) attacks that have significantly impacted end users by effectively knocking many websites temporarily off the Internet.
- DNS tunneling: The DNS can be abused to tunnel information through secure firewalls and is often used to coordinate botnets and other malware.
- Centralization: Blockchain is decentralized by nature, which would eliminate the current centralized model of trust.
While a DNS based on blockchain could result in a more democratic and less centralized version of the DNS, it is still in its infancy. The DNS, for all its flaws, continues to run smoothly, and efforts are continually being made to ensure that it is governed in a way that is fair and respectful of the needs of everyone. But who knows what the future of DNS, and of the Internet itself, might be!
